Cryptolocker is one of the most dangerous viruses of recent years. When it infects your PC, it “kidnaps” documents and requests money for their retrieval. But what happens if you don’t pay?
Cryptolocker is a ransomware trojan that infects Windows XP, Vista, 7, and 8. It disguises itself as a ZIP or PDF attachment, but is also transmitted by remote if a PC has been previously infected by a Trojan style “botnet,” which leaves the door open for remote control and external infections.

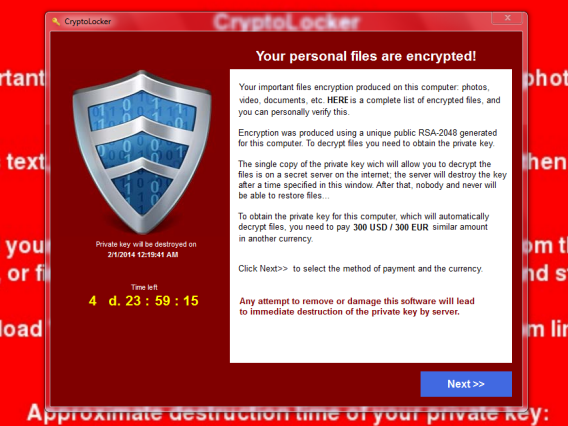
Cryptolocker kidnaps documents with a secret key
When executed, Cryptolocker is installed in the program folder and starts to encrypt LibreOffice and Office documents, PDF files, photos or illustrations, making them inaccessible. Files are encrypted with a key that only the authors of Cryptolocker have, making recovery impossible.
File that are infected by Cryptolocker become unreadable due to encryption
At the same time, CryptoLocker discloses its threat: if the owner fails to pay a sum of money within three or four days, the key to the files will be deleted forever, and the files can no longer be recovered. It’s like locking someone up in an indestructible cell and throwing away the key.
Files can’t be rescued without paying up
If the poor user agrees to pay the sum of money, which can be up to three hundred dollars, Cryptolocker decrypts the files, but not always. Payment can be made via MoneyPak, Ukash, and most recently, through Bitcoin, a virtual currency whose transactions are made without control.
The payment methods accepted by the Cryptolocker virus make identifying its creators difficult
Any attempt to make a fake payment reduces the time available to save the files. To “help” those affected by the virus, the creators have even put a “Support” address at the bottom of the screen that Cryptolocker activates on the infected PC; this web address contains the version of the decryption tool.

The Cryptolocker “support” page
The system devised by these criminals is pretty close to perfect: if the user doesn’t pay, the files cannot be recovered. The encryption used is too strong, and even a sophisticated cryptographic attack would take a very long time to decipher any of the locked files.
If someone doesn’t have their files backed up, they’ll end up paying.
What to do if your PC is infected by Cryptolocker
If you see the Cryptolocker screen, disconnect the device from the network so that the virus cannot encrypt more files or communicate with the creators. Disconnecting the internet connection also keeps your files in Dropbox or Google Drive from being overwritten with infected copies.
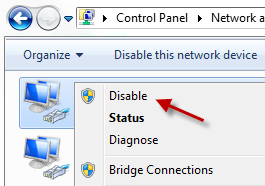
A quick way to disable the connection is to go to the control panel and disable the network device
Then, you have to ask yourself what you want to do: either pay the ransom, or remove the virus and attempt to recover the files. If you opt for payment, you are at the mercy of criminals, and recovery is not guaranteed. While there are many reports that say that the decryption occurs within hours of payment, others say that the recovery process is full of bugs. I would not recommend paying.
The Cryptolocker decryption tool only works if you’ve paid the ransom.
Whatever your choice, the best you can do is to get a list of infected and encrypted files. To do this, you can run the ListCrilock tool, which creates a TXT file with all the files encrypted by the virus. Another program that does the same is CryptoLocker Scan Tool, which looks for files infected by the virus and tells you if they need to be recovered.
CryptoFinder looks for infected files and tells you if they can be recovered or not
The manual option is to open the Windows Registry Editor (Start > Run > Regedit ) and type in HKEY_CURRENT_USER\Software. There, you will see a folder with a numbered subfolder containing the names of the files: this is Cryptolocker’s. Some of these files may not yet be encrypted and can be recovered. For the rest, you can only search your backups.
How to remove the Cryptolocker virus from your PC
Removing Cryptolocker is quite simple, in part because the creators of the virus make the victim terrified enough so that they don’t want to eliminate the only way to recover their files. Luckily, there are several ways to recover your files, but you must first remove the virus from the system.
brightcove.createExperiences();
In my case, I used Norton Power Eraser to remove Cryptolocker, a powerful anti-trojan that Symantec distributes free on its website. I copied Norton Power Eraser to the computer via removable storage, executed it and, upon completion of the scan, received a confirmation of the deleted files.

After the reboot, all traces of Cryptolocker were gone (it had only been the virus screen, which in itself is completely harmless and can be changed without problems).
Other tools that work are Malwarebytes, ComboFix and RogueKiller. Traditional antivirus solutions have trouble identifying Cryptolocker as an infection, especially with the speed with which new variants appear, but they are being constantly updated to account for this.
Recovering files infected by Cryptolocker
Cryptolocker only attacks documents found on the PC and on network drives. It doesn’t attack files that are on disconnected drives or servers that are on the internet, nor does it attack archived documents. Its main target is files that are on business PCs.
File extensions that Cryptolocker attacks include: .odt, .ods, .odp, .odm, .odc, .odb, .doc, .docx, .docm, .wps, .xls, .xlsx, .xlsm, .xlsb, .xlk, .ppt, .pptx, .pptm, .mdb, .accdb, .pst, .dwg, .dxf, .dxg, .wpd, .rtf, .wb2, .mdf, .dbf, .psd, .pdd, .pdf, .eps, .ai, .indd, .cdr, .jpg, .jpe, .jpg, .dng, .3fr, .arw, .srf, .sr2, .bay, .crw, .cr2, .dcr, .kdc, .erf, .mef, .mrw, .nef, .nrw, .orf, .raf, .raw, .rwl, .rw2, .r3d, .ptx, .pef, .srw, .x3f, .der, .cer, .crt, .pem, .pfx, .p12, .p7b, .p7c.
Once you’ve disinfected your PC, the best thing you can do is use one of the most interesting “secrets” of Windows, known as shadow copies, which are previous versions of files that Windows stores each time a file is modified. To access this feature, all you have to do is right click on a file and open the Properties.
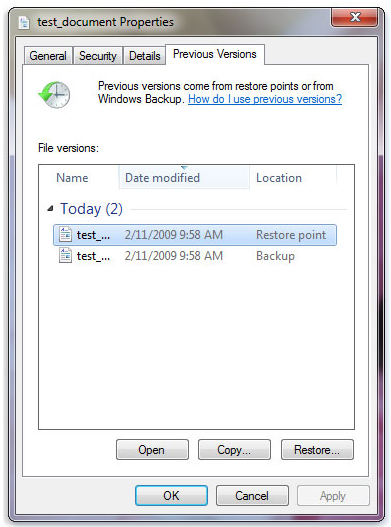
In the Previous Versions tab, you’ll see the different versions that Windows has stored. Select the most recent backup that predates the infection, and click to restore. A fast and convenient way to access all Shadow copies on the hard disk is using the free tool ShadowExplorer.
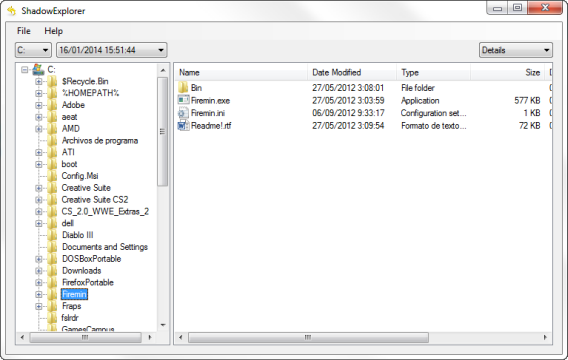
Shadow Explorer is very easy to use. Simply choose the drive, the date of the copies (which is in the drop down menu next to the drive), and then browse the folders and files. Copies are extracted with a right click on the file and another click on “Export”.
Another option to recover files is to use a previous backup that has been stored on a disconnected hard drive, a remote server, or on DVDs. Files stored in Dropbox, SkyDrive, or Drive are also good candidates for recovery.

When you recover a copy from Dropbox or Google Drive, you should make sure that it’s not one of the infected copies. Both applications have a version history for each document. In Drive, for example, it’s File>See revision history. From there you can retrieve the desired file.
Preventing Cryptolocker infections
Its creators designed Cryptolocker with two assumptions in mind: users open all attachments, and no one keeps recent backups of their documents. Your task is to dismantle this myth. To do this, you have to strengthen your security policies (or those of your business) .
For starters, be wary of suspicious emails. If it’s an email you’re not expecting, then don’t open any attachments for any reason. The same applies if you’re using webmail: if you haven’t asked for it, don’t click on it. This rule will prevent most opportunistic infections, which is the primary means of spreading the virus.
Gmail detected a virus which prevents it downloading (image: AskDaveTaylor)
Those who are seriously concerned can use the tool CryptoPrevent to disable the type of permissions that the virus uses to install itself. The tool modifies the Windows security policies to prevent a program being able to run from the Application Data folder (AppData).
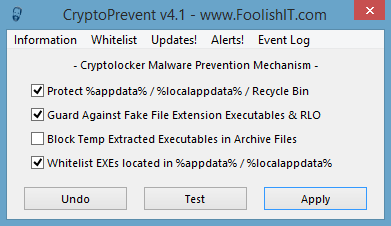
To run CryptoPrevent, check the first, second and fourth boxes so that existing programs in the folders can continue running. The “Undo” button allows you to undo the operation, a useful feature if you add a new program or if this patch creates more difficulty than security.
Finally, if you haven’t already, you should create your own backup plan. According to the firm BackBlaze, over 30% of users don’t have working backups of their documents, and only 10% make daily copies. You must configure a backup system for (at least) your most vital documents.
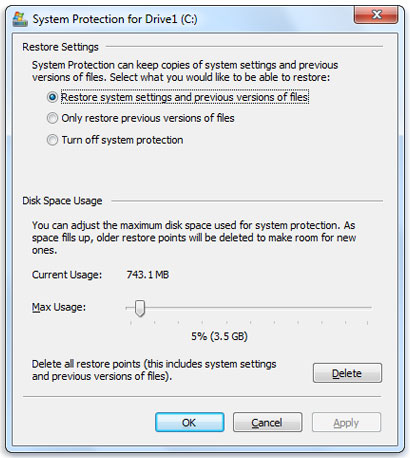
The Windows shadow copies are activated from the System Properties menu, which you can access by right-clicking on the My Computer icon, and also from the Control Panel, in the System section. The system protection part is one that allows you to enable the “shadow copies” and define how much space to allocate to them.
Cryptolocker is more dangerous than the Police virus
We all remember the dreaded REVETON, the virus from the police that caused panic in millions of homes and offices. The virus displayed a message that seemed to have been drawn up by the police and urged victims to pay money in exchange for not being prosecuted for horrific crimes. But the virus didn’t touch any files.
Cryptolocker is more harmful. In late 2013, it was estimated that it had already infected a quarter of a million PCs. Since Bitcoin transactions can be analyzed, experts discovered that cybercriminals are earning tens of millions of dollars because of this virus.
The way Cryptolocker infects PC is conventional, and can be stopped in its tracks if you take the precautions I’ve listed above. The most important lesson, however, is that you need to update your backups. Think of your data as your assets, and keep them just as safe.
Have you been infected by Cryptolocker?
Related Articles: