A lot has been said about the NSA scandal, and its easy to get carried away when it comes to Big Brother and government conspiracy theories, but what exactly does the NSA scandal mean for our privacy, and how worried should we really be?
Big Brother is watching like its 1984
The NSA is capable of decoding anything we transmit online: bank transactions, emails, documents. According to whistleblower Edward Snowden, the NSA can read virtually anything.

But how exactly does the NSA overcome the firewalls that supposedly protect our privacy online? We don’t have all the technical details, but according to Snowden, the NSA have managed to interfere in the development of encryption standards, forcing big companies to weaken their encryptions, supply them with data or provide back door access.
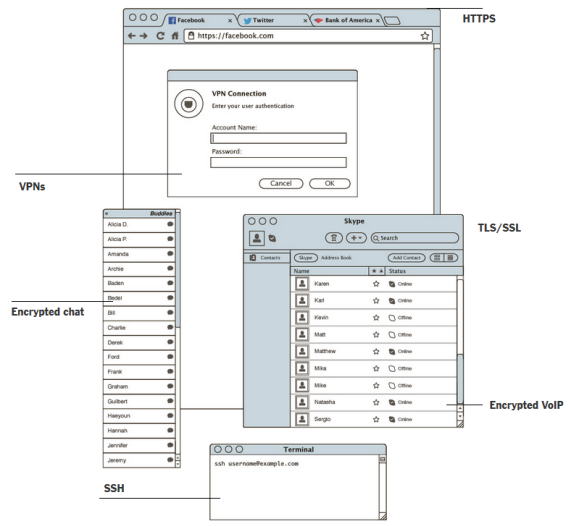 These are the protocols which, according to Snowden, the NSA can easily overcome (source)
These are the protocols which, according to Snowden, the NSA can easily overcome (source)
Luckily, Snowden recently confirmed that it is in fact possible to use secure encryption systems. Bruce Schneier, a well-known figure in the stealth field of cryptography, said that the math behind encryption keys is powerful, and that no computer, not even a quantum supercomputer (basically, a really powerful computer), would be able to break a key like the one we use every day to browse Facebook.
You’re probably not a target
Whatever tapping system is being orchestrated by the NSA, the probability that you’re the target is quite low. Of course, the NSA is on the defensive, trying to rationalize its efforts.
If you don’t have anything to hide though, then you don’t really need to worry, and if you live outside of the US, then you’re most likely in the clear (although the scale of the NSA’s monitoring is definitely global and affects all types of devices, where it actually reaches is not clear).
You’re not defenseless
We don’t know exactly how the NSA managed to outsmart the encryption systems in place on web browsers and cell phones, but one thing is clear: they still can’t break the most powerful encryptions. They can only get around them.
Like we mentioned in our ‘10 apps to secure your online privacy‘ article, there’s a ton of useful tools which, when used properly, will improve your privacy and security without making you compromise the way you use the web.
Secure browsing
- Tor, the system for browsing anonymously, has been noted as hackable by the NSA, but using it is still better than not using anything at all if you want to maintain some anonymity.
- Some browsers are more secure than others: epic browser, for example, only works in incognito mode, and has a proxy to anonymize your connection.
Email and messaging
- For email, solutions like GnuPG or PGP are still absolutely valid. Other options? Try HushMail or CounterMail.
- There are mobile apps which allow you to chat privately, either by destroying the messages, using encryption, or both.
Keeping a low profile is recommended
Being excessive with your security and encryption efforts could actually raise red flags and make you a target. Only use encryption when you need it – using complicated anonymizers when you’re sending your wife the grocery list, for example, is not recommended!
According to info leaked by Snowden, the NSA keeps encrypted data for longer, precisely because of the risk it could potentially pose. Their logic is simple: “If you use encryption, you have something to hide”.
You should limit the use of encryption to messages with sensitive information that can only be sent electronically and need to be protected. In the majority of cases, you won’t need to encrypt them simply because nobody is actively listening and you theoretically having nothing to hide.
So, to encrypt, or not to encrypt? That seems to be the question. The answer: use your own judgment to decide what really needs protection and what isn’t as important. The unfortunate part is, we now have to think about it.
Will you think twice about using encryption?
Original article by Fabrizio Ferri-Benedetti, published on Softonic ES.

