Passwords seem like the be-all and end-all in our current lives, logging us into our computers at work, unlocking our cell phones, or letting us withdraw money from our bank accounts. We’re then left with the unfortunate task of remembering all of these passwords and, on top of that, they’re sometimes not even as secure as we think they are. Are there alternatives? Yes, but they’re still a work in progress.
Our society is based on property, privacy, and confidentiality, and identification is a basic security principle: if you’re not who you say you are, your access should be restricted. Our life is full of keys and objects that certify our identity and access to property. It’s neither good nor bad: it’s just the way things are. How did it all begin?

Passwords: a legacy of the past
In computer science, the problem of identification and belonging to a virtual group first appeared with multiuser computers, large machines to which dozens of people were hooked up to at the same time. Passwords were invented to keep a user from impersonating another user and accessing data that didn’t belong to them.
 The invention of computer passwords is attributed to Fernando Corbató (source)
The invention of computer passwords is attributed to Fernando Corbató (source)
The fact that, historically, computer systems were accessed almost exclusively through keyboards is the basis for the clear text passwords in use today: a password could only be a string, but not too long, since available resources were very limited when passwords were invented. The proliferation of UNIX systems for accessing the internet in university environments solidified the use of this security mechanism in the early nineties.
Passwords: economical, yet problematic
Passwords are a very convenient identification system for any type of computer, since text input via a keyboard is available everywhere: there are very few computers without a keyboard, and it’s easy for operating systems to store and manipulate text strings like the ones used for passwords. The technology behind text passwords is simple, reliable, and available for use by any operating system and user, well meaning or not.
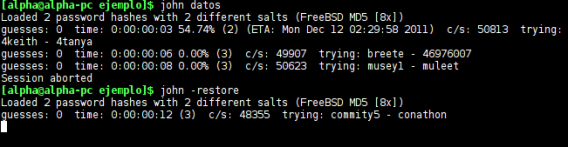 John the Ripper can easily process thousands of potential passwords per second (source)
John the Ripper can easily process thousands of potential passwords per second (source)
This also means that text-based passwords are inherently weak. This isn’t due to the systems that manage them, but rather to human beings: our brains have difficulty remembering long strings of letters and numbers. As a result, we tend to generate weak passwords that are easy to remember or that are associated with things we already know. So we use passwords such as “foo”, “123456” or even “password”. Why is this a problem? Decoding short, obvious, easy-to-guess passwords is a simple matter for the many programs available for this purpose. Since these passwords allow access to accounts such as Facebook and Twitter, we’re opening ourselves up to trouble.
Many attempts to raise public awareness
Years of awareness about the importance of strong passwords hasn’t made much of a difference. Weak passwords continue to be used, even though we know we’re courting disaster. And when a web page or application forces us to follow minimum standards of length and variety (uppercase, numbers, and special characters), we repeat the use of the same “safe” password we’ve used in other places, which allows a hacker to gain access to many accounts at once. That’s all because we put convenience before security. Unfortunately, that’s pretty standard human behavior, so it’s not likely to change anytime soon.
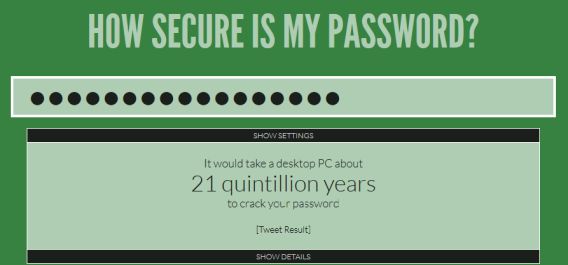 The web site How Secure is My Password tells you how long (seconds, minutes, etc.) it would take to guess your password.
The web site How Secure is My Password tells you how long (seconds, minutes, etc.) it would take to guess your password.
Security experts and psychologists recommend using mnemonic techniques to make it easier to remember your password, associating a character with a word or using phrases of songs or poems as a long password. Another way to avoid problems is to use a password manager like Dashlane. In addition to remembering your passwords in exchange for creating a master key, it can instantly generate very strong passwords and associate them with the accounts you use.
Alternatives exist, but haven’t taken off
The problems associated with text passwords were soon discovered and alternative identification systems were developed. Today there are a variety of systems that are used as substitutes for, or that complement, passwords. They’re divided into four broad categories: things you know, things you have (tokens), things you are (biometrics), and things you do.
Keys you know (“things you know”)
Passwords are a basic type of cognitive key: they’re something we know by heart. But our memory is not limited to words. We can recall faces, geometric patterns, pictures, and life events with equal or greater ease, By associating passwords with memories and emotions, those keys are remembered almost effortlessly.
 In Windows 8, you can easily create a picture password
In Windows 8, you can easily create a picture password
Android security patterns and Windows 8 pictures are two examples of cognitive keys that are easier to remember than traditional passwords, and are more impervious to attempted theft. However, the classic personal questions (“What was the name of your first pet?”) are strong only to the extent that your answer is not obvious or used too often.
Keys you possess (“things you have”)
 The key to your home is a physical password that you carry with you at all times. Your debit card PIN is also a key, as it gives you access to your cash. The advantage of such an identification system means you don’t need to remember a complex password, since the key in your possession is enough to secure your property, whether it’s your data or a physical object.
The key to your home is a physical password that you carry with you at all times. Your debit card PIN is also a key, as it gives you access to your cash. The advantage of such an identification system means you don’t need to remember a complex password, since the key in your possession is enough to secure your property, whether it’s your data or a physical object.
In computer science, physical keys (such as USB dongles), have traditionally been used as copy protection systems, but now, thanks to mobile phones, they’re now used to supplement security systems in what’s known as “two-step verification“, i.e. the joint use of a traditional password along with a code sent to the phone.
Biometric keys (“things you are”)
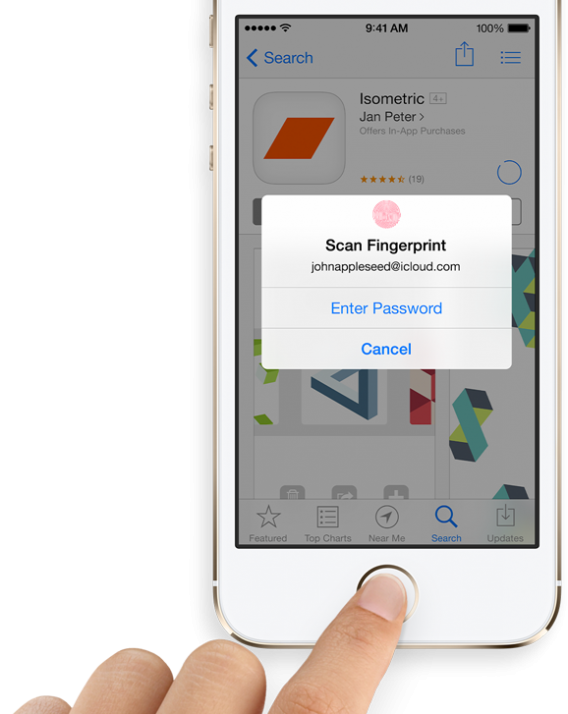 Your body is unique. Your fingerprints, eyes, voice, and face can only belong to you, and nobody can take them (at least not with the same ease that a key can be stolen). What makes you recognizable to others can also make you recognizable to any computer properly equipped with biometric sensors. Android’s facial recognition and iOS 7 with its fingerprint reader are two prominent examples.
Your body is unique. Your fingerprints, eyes, voice, and face can only belong to you, and nobody can take them (at least not with the same ease that a key can be stolen). What makes you recognizable to others can also make you recognizable to any computer properly equipped with biometric sensors. Android’s facial recognition and iOS 7 with its fingerprint reader are two prominent examples.
On paper, biometric identification systems seem to have everything needed to replace passwords: you don’t have to remember anything, they can’t be stolen (easily), and there are no complex passwords… In practice, however, these systems can also be less reliable.
Codes of conduct (“things you do”)
Your location, what you’re doing, and your usual behavior are pieces of information that can be used to complement traditional identification systems. Many of these mechanisms are automatic: for example, a page can prevent password access if it detects that it’s being accessed from an unusual place or from an insecure environment.
The use of this kind of identification, however, isn’t common, perhaps because of the limited control a user has over it. And it’s a psychological disadvantage: if we don’t “have” a key, we feel less secure.
What’s the ideal security system? Combining key types.
No single system is foolproof. Using more than one identification system is the best way to increase the security of your data. Even if one of your security systems is compromised, you’re still protected.
Multi-step identification systems still have implementation problems that will be difficult to overcome in the short term. Only large software and web service companies can afford to implement such systems, especially if they involve the use of biometric sensors or physical keys. And users are used to dealing with only one system…until now.
The popularity of two-step verification systems such as those used by Google, Facebook and Twitter, as well as Apple’s recent introduction of biometric screening, are, however, very promising signs for moving beyond traditional password identification systems. In the future, it’s likely we’ll witness an explosion in the use of multi-step identification systems. We can only hope.
Do you think passwords will be around forever?
Original article written by Fabrizio Ferri-Benedetti on Softonic ES.

