Some viruses copy everything you type, record video with your webcam, and listen through the microphone. In other words, they’re PC spies. In this article, we’ll tell you how to spot them, how to prevent attacks and how to react if you’ve been infected.
A spyware virus is a type of computer virus that, instead of deleting files or getting cloned, aims to steal information. To bypass security controls and antivirus software, the spyware virus poses as a legitimate and valuable application, when in fact it’s being controlled remotely via the internet.
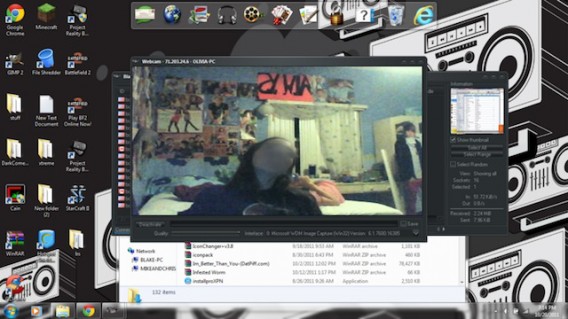
What a cyberspy sees when it turns on the webcam of an infected PC (source)
Fake antivirus programs, also known as rogueware, are a classic example of Trojan virus. But there are other spyware programs that can access a computer without the victim knowing it. When these viruses are created by governments and security agencies, they’re called govware. According to Ed Snowden, the NSA was planning on using these programs to spy on citizens.
What do spyware programs do?
Spyware programs were created to steal data without the victim knowing it. They are invisible, and try to draw as little attention as possible. Sometimes the spyware can even pose as a legitimate application. Depending on the type and complexity of the malware, a spy virus can:
- Record all keystrokes (keylogger)
- Take pictures or videos from your PC webcam
- Take screenshots of your desktop
- Record sounds from your microphone or sound card
- View the victim’s screen (remote viewing)
- Take full control of the computer (remote control)
All of these have one thing in common: they need an internet connection. Without the internet, the spyware can’t do any of the above. Now that everyone seems to have a high-speed internet connection, however, spyware is more harmful than ever, as it can steal and send a much larger volume of data.
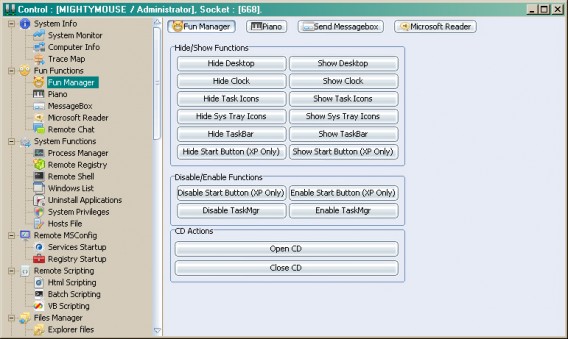
The Fun Manager virus can do anything it wants on the victim’s PC (source)
How does a PC get infected with spyware?
Generally, spyware programs take advantage of their victim’s trust to access the PC undetected and without forcing their way in (dodging antivirus and firewalls). To avoid Windows firewalls, they use a range of strategies:
- They pose as legitimate or popular applications
- They run from a camouflaged attachment
- They come with pirated programs (i.e. games)
- The victim is persuaded to install it (social engineering)
Sometimes hackers use well-known remote admin applications, although they are modified to avoid raising any alarms. Other times, the spyware takes advantage of the security vulnerabilities to enter the system unnoticed by the antivirus.
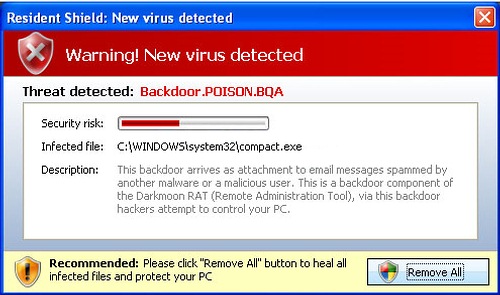
A fake virus warning: the user clicks and the PC gets infected (source)
How can you detect a spyware program?
Quick answer: with a good antivirus. Long answer: be very careful. Sometimes the antivirus software fails or isunable to identify subtle threats such as spyware. As a result, you’ll sometimes only be able to identify infection if you notice specific ‘signs’.
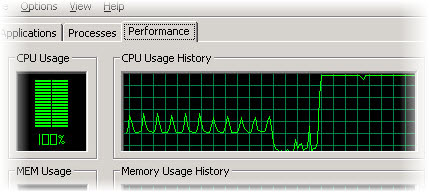
An unexplained high CPU usage could mean that your PC has been infected (source)
For example, many remote access Trojans increase the CPU usage, making your PC slow. Some disable the visual themes to enable remote viewing. And other malware eventually interferes with your computer’s hardware. Look out for the following signs:
- Programs have become slow or unresponsive
- The mouse pointer moves erratically
- The light from your webcam turns on intermittently
- Windows lose their transparency
- Strange icons appear in the system tray
- Navigation speed is slow
- Windows open by themselves and you can hear strange sounds
What some spyware software can do is so spectacular that some victims even think their computer has been ‘possessed’. But these signs by themselves are not enough to confirm a spyware infection, as they could be caused by other issues, such as hardware failures or application problems.
A strange process in the Task Manager is a sign of a possible virus (source)
In some cases, whoever is controlling the PC posts messages or contacts the victims to have fun at their expense or even blackmail them. When this happens, the infection is clear and you need to take immediate action.
If you discover spyware: unplug and report
If you believe that there is someone spying on your PC, unplug the device from the internet to stop the intrusion going further. The best thing to do is to remove the network cable, or switch off the wireless network adapter (WiFi).

As soon as you detect the spyware, disconnect the PC from the internet
Then you should collect all the information you can about the intrusion. All the evidence you can provide will be useful for the authorities, from screenshots to emails or files left by the intruders. Even the smallest signs of intrusion can contribute to the investigation.
Liutenant Angel Flores, from the Spanish Civil Guard Cybercrime Department, recommends taking the PC to the police station so that agents can certify the authenticity of the messages. “If there has been an exchange of emails for blackmail purposes, it’s useful to include their header in the copy. And if the person comes to the station and opens the email in front of us from their PC, we can verify its authenticity.”

Spanish computer detectives work on copies of the hard drives, not the original
If you decide to go to the police, your PC could be sent to a forensics team to collect all the information on the intrusion, which means you won’t be able to access your PC for a short time. “We make a copy of everything that’s on the PC.”, says Lieutenant Flores, who recommends us to “not touch or remove anything” and take the PC to the authorities.

Programs like OSForensics are used by the authorities to clone a PC
After making the copy, the PC will be returned within a day or two. It’s a minor inconvenience, but you’ll get your computer back intact. “The problem is that people don’t say anything. An official police report should be made. Otherwise, we’re even helping the cyberstalker. If you start by thinking ‘I’m not going to take it, because then I’ll be without a computer for a week’… then you’ll end up doing nothing”, says Flores.
Spyware infections can be prevented
Spyware attacks can be prevented if you take precautions and take care of the security of your computer and your accounts. The more careful you are, the more difficult it’ll be for the cyberspy to find a way into your computer:
- Install a good antivirus and keep it updated
- Install a good firewall to block and monitor connections
- Use a standard user account instead of an administrator account
- Keep portable antivirus at hand for a ‘second opinion’
- Don’t open suspicious emails and attachments
- Don’t install extensions on your browser without knowing their origin
Many of the tips we’ve given Windows XP users to keep their system safe after support ended can also be applied to other Windows versions. The goal is to shield the PC from all types of intrusions. But it’s also common sense:
- Be careful when you chat with strangers, don’t accept their files
- Share files safely to avoid sharing private data
- Strengthen your network security to prevent intrusions via Wi-Fi
- Enable two-step verification on all your accounts
Our advice: don’t let panic take control!
Computer spies become stronger with the ignorance and fear of their victims. If you discover that you have been the victim of cyber bullying or computer spying, remain calm: even if you are afraid, the blackmail threats of your stalkers have little or no real impact. You now know what to do: if you are a victim of cyber espionage, unplug, collect info and report.
The author thanks the Spanish Police for their help.
Have you ever been spied on? Follow me on Twitter and tell me: @remoquete


