Every time you install an app, you have to accept permissions. But what are you really agreeing to? Are they dangerous for your privacy and security? The recent drama over Facebook Messenger permissions had people freaking out over how sinister some of them sound.
To use the camera, internet, and other resources on your mobile phone, Android apps ask for permission. Apps are only installed if you agree, and you can only accept or reject all of them at the same time (it’s an all-or-nothing system). The problem arises when permissions are combined: to review them all is exhausting, so you just end up accept them without looking.

To accept these permissions without thinking can have consequences, such as SMS being sent without you knowing, or the theft of personal data, as happened with the Balloon Pop 2 virus. It takes less than a minute to check the permissions, a minute that can save you from major problems in the future (like having to change all your passwords).
Below, I’ll detail the current permissions that apps request prior to installation, and I’ll explain why they can be dangerous and what you can do to avoid future problems.
In-app purchases: beware of extortion and frauds
In a game like Candy Crush, for example, you can buy items that will help you level-up, but there are apps that use this system to extort money under all sorts of promises.
Fakedefender was a fake antivirus that showed security alerts and promised to clean the phone after making a purchase from the app. Another case is when a free game has in-app purchases: if a child is using the app, they may be fooled into buying premium currency.
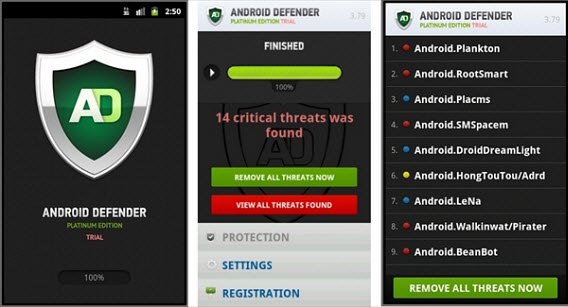
Android Defender, the fake antivirus that extorted users with in-app purchases
To avoid problems related to in-app purchases, enable password protection in Google Play. That way, you’ll avoid impulse purchases. Above all, don’t be fooled by false promises.
Mobile data / Wi-Fi: the gateway for data theft
Both sections are relatively harmless, as they manage how apps are connected to the internet. Any app that needs to go online will ask for these permissions. They only become dangerous when they are combined with others, since they give the green light to an app to send data outside.
The pair “read contacts” and “mobile data,” for example, should worry you. Why would an address book need access to internet? Maybe it’s for advertising reasons, but you must be sure about it. When in doubt, you can choose to block the connection with a firewall (which is also effective to disable advertising in some games).
Device and app history: your history and bookmarks are there
These permissions allow access to phone data, such as sites you’ve browsed, your favorites, and what apps you’re running. A web browser, an app manager, or a social network needs to access your app and bookmark list to look up info or modify it, but not a game.
Chrome browser will ask you for permission to access your device and app history list: it’s ok
The risks to your privacy are obvious: this is the kind of data that the NSA or others want to be able to track your browsing history. Before installing any app that wants these permissions, you should ask yourself if it’s necessary.
Identity and accounts: your accounts available for any app
Identity permissions let apps access personal data, such as accounts you have on your phone. It makes sense for social network apps such as Facebook or Twitter, but not when this info has nothing to do with the main purpose of the app. Among other things, a virus that makes use of this permission could possibly delete your accounts.
Contacts / Calendar: careful with sharing your address book
The greatest danger of these permission lies when they ask to access your address book and calendar events. A malicious app could extract email addresses or phone numbers and delete calendar events without your permission (and even invite people without your permission).
The FireLeaker virus stole phone numbers and email addresses and sent them to a server controlled by cyber criminals, then sold that data to companies that send spam in emails or SMS messages.
Location: does a game need to know where you are right now?
This set of permissions provides access to location sensors such as GPS, useful for maps, guides, and apps that add location data to your photos and publications. If you think that this permission doesn’t make sense for a particular app, be suspicious.
Besides consuming battery, collecting location data will put your privacy at risk. The TigerBot malware, discovered in 2012, sent the GPS location of the mobile along with other data, such as call recordings and images.
Tigerbot is a Trojan that hid under the generic name ‘System’
SMS: be careful with apps that send expensive short messages
If you see these permissions, ask yourself why an app needs to receive, read, or send text messages. Some receive SMS to confirm your registration to a service, but other times, sending expensive text messages can be a lucrative fraud.
In 2014, Panda Labs discovered that a diet app, downloaded by 300,000 people, subscribed its users to an expensive SMS payment plan through a simple and effective fraud.
Phone: when an app can dial and call for you
These permissions are intended to allow apps to manage or initiate calls. Messaging apps such as WhatsApp or LINE, call blockers, and voice mail apps use these permissions.
But in apps where using the phone makes no sense, these permissions could indicate some kind of hidden call charges. MouaBad malware, discovered in 2013 by Lookout, allowed hackers to make very expensive calls without the device owners noticing.
MouaBad.P that could remotely call premium numbers
Photos, data and files: what if they read your saved files?
If an app needs to store files, it will ask for permission to modify or remove content. It’s difficult to know when this will be used for malicious purposes, such as stealing or deleting data.
Some viruses can take over the phone and send pictures and other files over the network. The Pixer app, which can still be downloaded from Google Play, deceived users to accept permissions and then uploaded photos to its servers.
Camera / Microphone: permissions 007 would have loved to have
When you allow an app access to your camera and microphone, it can take pictures and videos as well as record sounds. Makes all the sense in the world with apps like Instagram, Skype, or Facebook. In other cases, watch out.
PlaceRaider, an app capable of taking random photos and recreate entire rooms
The PlaceRaider app is an example of the danger of accepting permissions without thinking. Created by a team of researchers from the States, this app can take your pictures without permission and recreate rooms: you have given permission to be spied on.
Device ID and call data: your phone’s ID
Under this mysterious name, Android gives the apps permission to know your phone. Among others, it includes getting data like the IMEI number, which is the phone’s ID. It’s quite easy to get it.
An example of the data that can be taken with the ID permissions
With a valid IMEI, someone could clone your phone and make calls; the bill would come to you. It could also block your number if it tells the phone company that it has been stolen. The BadNews virus is an example of this type of malware.
Others: a very dangerous hodgepodge
Besides the typical Android permissions, an app can request other unique permissions. It’s very important that you review this list whenever you see it. Among other permissions, there are some that are particularly sensitive, such as reading messages on your social networks, having full network access, or having control over the device. There are no limits: the security of your device and data could fall apart due to that permission hidden under Others.
The golden rule: research and use permission tools
If you think that a permission doesn’t make sense, ask the developers: you can send them an email from Google Play or leave a comment and wait for them to reply. The comments sent by other users (and the app’s score) are also important to know if an app is safe and reliable. Don’t install anything suspicious without having checked it before.
What about the apps you’ve already installed? There are tools that are dedicated solely to checking the permissions for all the apps installed on your phone or tablet. A good example is F-Secure App Permissions, which scans all the permissions of the apps you are using and tells you the most suspicious cases for you to decide what to do with each.

F-Secure App Permissions gives a score to each app according to the permissions requested
After reading this article, you might think that permissions exist only for evil purposes. It’s not true: many legitimate apps would not work without them. The way Android handles the permissions, however, is not adequate, as it leads to dangerous oversights. It’s just too easy to accept an objectionable permission.
Related Articles
How to protect your online identity and why you should care
Why Facebook Messenger permissions aren’t unique or dangerous
The Windows Store is full of fraudulent apps and Microsoft doesn’t care
‘Anonymous’ social networks like Secret fail to provide anonymity
Follow me on Twitter: @remoquete


