A newly discovered vulnerability within the command line which runs in the background of Mac OS X, Linux and many Unix based system lets hackers remotely execute commands to computers and websites. Bash has been around for twenty-five years but this vulnerability was just recently discovered and has the potential to exploit computers, devices, websites and more. We will likely continue seeing damage from the Shellshock Bash bug for years to come.
What is Bash and why are so many things using it?
Without getting too technical, Bash is basically an interpreter for computers, allowing users to execute commands on Unix and Linux systems. It is used on a variety of devices because the software is open source and is the industry standard for web servers.
 Image credit: Netcraft
Image credit: Netcraft
Over half of all web servers in the world are running Apache, which is a web server application responsible for HTTP, or hypertext transfer protocol. Apache is credited for the huge growth of the internet.
How is Bash being exploited?
Bash is allowing attackers to execute arbitrary code on affected systems without any form of authentication. This type of attack is called “code injection,” and there are many environmental variables for hackers to exploit.
As mentioned previously, many websites run on web servers that are vulnerable to the Shellshock Bash bug. This means entire websites could theoretically be taken down by it. Worse, there are tons of devices that support Bash like web cameras and routers. Home automation tools like networked lightbulbs and thermostats could be affected as well.
Good thing I’m using Windows.
While the Windows operating system isn’t directly affected, the devices you connect to your computer may still use Bash. The router you use to connect your Windows computer to the internet is most likely running an operating system that’s vulnerable.
Is this as bad as Heartbleed?
The Shellshock Bash bug is drawing many comparisons to the Heartbleed vulnerability discovered a couple months ago. While the vulnerabilities are completely different, the widespread effects of both attacks are comparable. We’ll be seeing the effects of both vulnerabilities for many years to come.
The difference is, Heartbleed only affected websites and services. The Shellshock Bash bug can affect sites, computers and many other devices.
Attackers know about the exploit and are already using it. Someone created an internet scanning tool to probe websites that are vulnerable to the Shellshock Bash bug. Ars Technica found over 2 billion sites that “fit the profile for the Shellshock exploit.”
We don’t know how far hackers will go. These hackers could possibly creating worms that can pass through firewalls and self-replicate, infecting a wide array of machines on a network without users noticing. Hackers could even snoop on your personal data once your machine is compromised using the bug.
For now, we’re waiting to see what attackers are going to do with the exploit.
What can I do to protect myself?
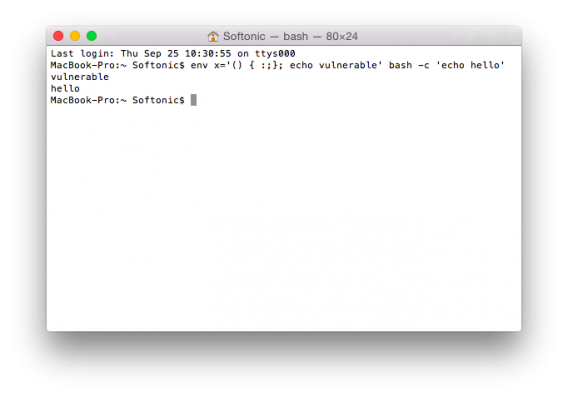
If you’re a Mac user and want to find out if you’re vulnerable, you can run the following script in the Terminal application (located in your Utilities folder).
$ env x='() { :;}; echo vulnerable’ bash -c ‘echo hello’
If the command reads “vulnerable” and “hello” then your machine is susceptible to the Shellshock bug. There’s a way to patch the vulnerability yourself by recompiling Bash but that’s extremely technical and not for the faint of heart. If you feel comfortable with the command line, head over to Stack Exchange for details about how to patch the bug. Mere mortals will want to watch closely for an update from Apple.
For most users, the best thing you can do now is to make sure you are running the latest software on all your devices. And I mean all of them. Check for firmware updates on your router, which most users tend to forget about. Consult the manual for your particular router to see how to update the firmware as each model has different steps.
Users will also want to watch out for any suspicious sites or emails that want you to install software. With this bug causing a huge stir, you can be sure hackers will be looking to capitalize on people’s fears by offering fake software solutions to “patch” your computer.
Beyond keeping your devices up to date and being careful online, control over this bug is largely out of your hands. You’ll have to wait for sites to patch the vulnerability on their web servers.
Related Stories
Why does a keyboard app need ‘Full Access’ to my iPhone?
Firefox and Thunderbird get ‘critical’ security updates
The next version of Android will encrypt your data by default
Updates for Adobe Reader and Acrobat fix security vulnerability
Follow me on Twitter: @lewisleong


